Cyber security attacks are any type of malicious activity that targets IT systems, or the people who use them, to gain unauthorized access to systems and data or information contained. In many cases, cybercriminals are criminals who want to exploit the attack to get money. In some cases, the intention is to disrupt operations by disabling access to IT systems, or in some cases directly damaging physical resources. The latter type of attack is usually government-sponsored and carried out by state actors, or hired criminals.
Cyber security attacks can be embattled at definite administrations or persons. Or they can spread naturally and affect many organizations regionally and globally. Often the targeted attack escapes from their target victims to become common problems in all organizations. The global attack on NotPetya in June 2017 may have had the effect of targeting attacks on Ukrainian banks and the services of state actors. It had a targeted impact on Ukraine. But it also spread globally and cost about $ 10 billion in cost to acquire IT systems and lost production according to articles including cleaning.
Following are the most common kinds of cyber security attacks seen today.
Malware – Cyber Security Attacks
If you have ever got an antivirus alert that appears on your screen, or if you have accidentally clicked on malicious email attachments, then call near malware. Attackers like to use malware to locate users’ computers – and, as a result, the offices in which they work – because they can work very well.

Malware states to a variety of malicious software, such as viruses and ransomware. If malware is on your computer, it can create all sorts of dangers, from controlling your machine to monitor your actions and clicking buttons to silently send all kinds of confidential information from your computer or network to the home of the attackers.
Attackers will use various methods to install malware on your computer, but in some cases, it requires the user to take any action to install the malware. This may involve clicking on a link to download a file, or opening an attachment that may look harmless (like a Word document or PDF attachment), but truly has a malware installer hidden inside.
Phishing – Cyber security Attacks
Of course, you can simply open a random attachment or click on a link in any email that comes to you – there must be a good reason for you to take action. Attackers know this too. When an attacker wants you to install malware or extract sensitive information, they often resort to subtle tactics or impersonations to get you to do something that you would not otherwise do. Relying on human curiosity and emotions, the crime of stealing sensitive information can be hard to break.
In a phishing scam, an attacker may send you an e-mail that appears to be from someone you trust. Such as your supervisor or your business partner. An email will appear legitimate and will be urgent (e.g. fraudulent activity detected on your account). In the email, there will be an opening attachment or a click link. When you open a malicious email attachment, you will install malware on your computer. When you click the link, we can send you a website that looks legitimate asking you to log in to access the important file. Unless the website actually a trap uses to enter your credentials when you try to sign in.
SQL Injection Attack
SQL (pronounced “sequence”) represents a structured query language; a programming language used to communicate information. Many servers store sensitive websites and services using SQL to manage data in its archives. SQL injection attacks target this type of server, using malicious code to get the server to disclose information that would not otherwise be possible. This is particularly true if the server stores private customer data from a website. Such as credit card numbers, usernames, and passwords (credentials), or other personal identification information, which is attractive and beneficial to the attacker.
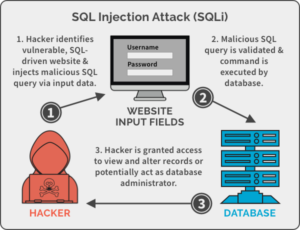
SQL injection attacks work by misusing any known SQL vulnerabilities that allow the SQL server to use malicious code. For example, if a SQL server is in danger of being attacked by injection, the attacker may go to the web search box and type a code that would force the site’s SQL server to discard all its stored usernames and passwords.
Cross-Site Scripting (XSS) – Cyber security Attacks
In a SQL injection attack, the attacker follows a compromised website to identify its stored data. Such as user authentication or sensitive financial data. However, if the attacker can target the users of the website, they may choose to attack the script. Similar to SQL injection attacks, these attacks also include injecting malicious code into websites. But in this case, the website itself not attack. Instead, the malicious code the attacker entered only in the user’s browser. When they visited the attacked website and follow the visitor directly, not the website.
One of the most corporate ways an attacker can use a script attack on a site is to insert malicious code into comments or scripts that may automatically work. For example, they may embed a malicious JavaScript link in a comment on a blog.
Cross-site scripting is Cyber security attacks that can seriously damage a website’s reputation by putting users ’information at risk without any sign that something terrible has happened. Any sensitive data a user sends to that site. Such as his or her personal information, credit card details, or other personal information. May be hijacked by cross-site scripting without the website owners realizing that there is a problem even from the beginning.
Denial-of-Service (DoS)
Imagine that you are sitting in a car on the road, and the road rush as the eyes can’t see. Usually, this street does not see more than a car or two. But the regional exhibition and the major sporting event ended at the same time. As well as this road is the only way for tourists to leave the city. The road cannot handle the large rush, and as a result, it overcrowds that no one leaves.
This is what occurs to a website through a denial-of-service (DoS) attack. If you overflow a website with more traffic than it is designed to manage, you will overload the webserver. It will almost certainly not be possible for the website to provide its content to visitors trying to reach you.
This can happen for no apparent reason. However, if big news explodes and the newspaper website is overcrowded with people coming out trying to find out more. But more often than not, this type of overcrowding is dangerous. As the attacker floods the website with a lot of traffic to block all users.
In some cases, these DoS attacks carry out on multiple computers simultaneously. This type of Cyber security attacks known as the Distribute Denial-of-Service Attack (DDoS). This type of attack can be challenging to overcome because the attacker comes from multiple IP addresses around the world. At the same time, making determining the source of the attack very difficult for network administrators.


0 Comments