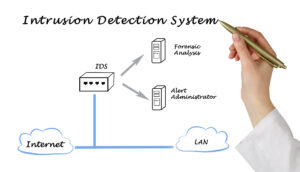
Intrusion Detection System (IDS) is a system that monitors network traffic for suspicious activity and alerts when that service is detected. While unnecessary detection and reporting are key functions, some access systems can take action when bad work or unfavorable traffic detected, including blocking traffic sent from suspicious Internet Protocol (IP) addresses.
You can IDS compare to an intruder (IPS) system. That looks for network packets to detect potentially harmful network traffic, such as IDS. But as a primary purpose for preventing threats once they detected, unlike receiving and recording threats.
How do intrusion detection systems work?
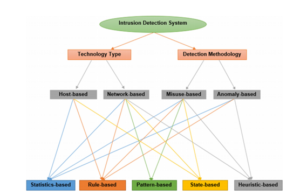
Intrusion detection systems use to detect malpractice to catch hackers before they cause real damage to the network. They can be network- or Host-based. The host-based intrusion detection system is installed on the client computer, while the internal access system is located on the network.
These systems work by looking for signatures of known attacks or deviations from normal activities. These deviations or inconsistencies pull up to the stack and checked in the tracking line of the application. They can better view events such as the Christmas tree scanner and system domain name (DNS).
IDS can be implemented as a software program that works on client hardware or as a network security tool. Cloud intrusion detection systems are available to protect data and deployment systems.
Different types of intrusion detection systems
IDS come in a variety of flavors and detect suspicious activity using a variety of methods, including the following:
The NIDS (network intrusion detection system):
It distributed locally or at points within the network, where it can monitor incoming and outgoing traffic to and from all devices on the network.
The host intrusion detection system (HIDS):
It works on all PCs or expedients in the network with direct access to the Internet and the internal business network. HIDS has an advantage over NIDS because it can detect unwanted network packets from within an organization or malicious traffic that has failed to detect NIDS. HIDS may also be able to detect malicious traffic from the host itself, such as when the host is infected with malware and attempts to spread other programs.
The signature access system (SIDS):
monitors all packets crossing the network and compares them to a database of signature attacks or malicious threats such as antivirus software.
The AIDS (anomaly-based intrusion detection system):
assesses network traffic and compares it with a fixed base to determine what is considered a normal network in terms of bandwidth, contracts, ports, and other devices. This type often uses machine learning to establish a basic and consistent security policy. It then warns IT, teams, against suspicious activity and policy violations. By detecting threats using a comprehensive model instead of specific signatures and symbols, the fraud-based detection method develops within the limits of the signature-based methods, especially in detecting novel threats.
Historically, access systems were classified as idle or active. An idle ID that has received malicious activity will generate a warning or log entry but no action; valid IDS sometimes called intrusion detection and detection system (IDPs), will generate warnings and log insertions. But may configure to take action, such as blocking IP addresses or blocking access to restricted resources.
Snort – one of the greatest extensively utilized intrusion detection systems. Is an open-source, freely available, and lightweight NIDS use to detect emerging threats. Snort integrates into most Unix or Linux (OSes) applications, with the available version of Windows as well.
The power of intrusion detection systems
Intrusion detection systems monitor network traffic to detect attacks by unauthorized organizations. The IDS does this by providing some – or all of these services to security professionals:
- Monitor the performance of routers, firewalls, key management servers, and files required by other security controls aimed at detecting, preventing, or retrieving cyber-attacks;
- To provide managers with a way to tune, plan and understand appropriate OS testing methods and other logs that are difficult to track or monitor;
- Deliver a user-friendly interface so that none pert employees can assist in managing system security;
- Including a comprehensive database of attack signatures that can be matched with information from the system;
- Identify and report when IDS detects that data files have been altered;
- Generating alarms and notifying security breaches; and
- We respond to intruders by blocking them or blocking the server.
Benefits of intrusion detection systems
Intrusion detection offer organizations several benefits, starting with being able to detect security incidents. IDS use to help analyze quantity and types of attacks; organizations may use this information to change their security systems or to use better-controlled controls. The intrusion detection system can help companies identify bugs or problems with the configuration of their network device. These metrics then utilized to assess future risks.
Intrusion detection systems can also help an enterprise gain compliance control. IDS gives companies greater visibility across all their networks, making it easier to meet safety rules. Additionally, businesses can use their IDS logs as part of the documentation to show that they meet certain compliance requirements.
Intrusion detection systems can also increase security answers. Since IDS sensors can detect network and device hosting, they use to scan data within network packets, as well as to recognize operating OS OSes. Handling IDS to collect this information can be much better than manual manipulation of connected systems.


0 Comments